By now most everyone in the IT industry has been informed of what’s known as the speculative execution side-channel attacks also known as the Meltdown and Spectre vulnerabilities. It is expected that variations of both methods of exploitation will be publicly available within the next few weeks. The proof of concept has been made available on GitHub.
https://github.com/mniip/spectre-meltdown-poc
These exploits are receiving so much publicity for one primary reason. The method of exploitation manipulates deficiencies in the speculative execution and branch prediction features designed to speed up execution in almost all modern processors developed since 1995. The Meltdown technique essentially allows an attacker to read Kernel memory from user space and the Spectre technique allows an attacker to read memory contents from other applications.
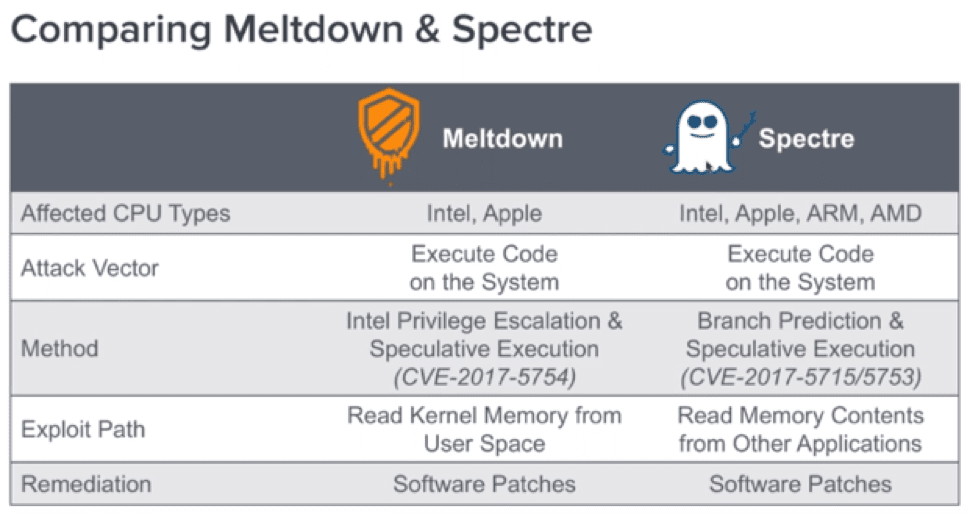
The potential for exploitation is very wide reaching as it affects all Windows and Linux OS types, Apple iOS, MacOS, Android, Chrome iOS and many more. These vulnerabilities affect many and almost all types of platforms to include standard desktops and servers, mobile devices and other 3rd party proprietary operating systems. Meltdown and Spectre are also of critical concern for service provider cloud offerings through AWS and Azure. Major companies like Google, Microsoft, and Amazon have known of these flaws since June and have been working tirelessly to patch systems before the vulnerabilities were disclosed to the public.
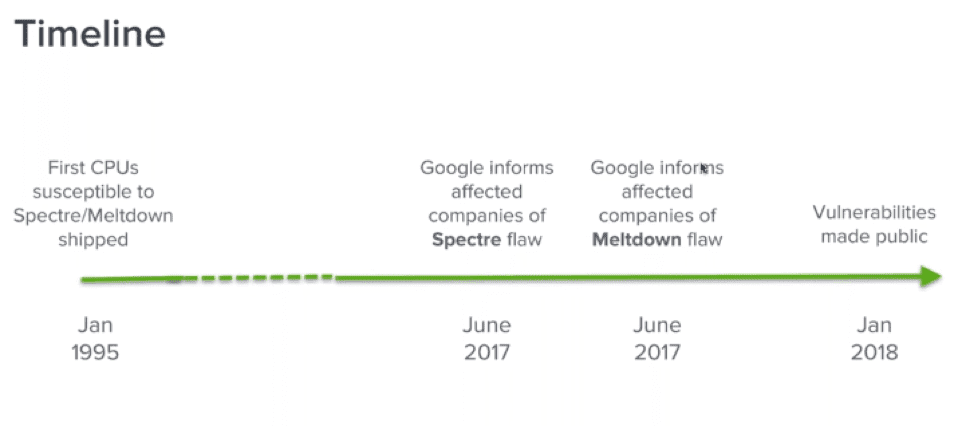
Microsoft patch KB4056892 released Jan 4th has covered most OS types but 3rd party proprietary operating systems have seen issues with performance, system slowdowns and crashes to include some of the AMD chipsets. The update includes internet explorer and Edge mitigations. Similar to the variants of popular SSL vulnerabilities like Heartbleed the security community expects new speculative execution variants discovered and used as exploitation techniques over the next few years.
https://support.microsoft.com/en-us/help/4056892/windows-10-update-kb4056892
Here at CyFlare, our security analysts are continually researching and monitoring the situation each day. Working with our partners and the security community to stay abreast new information and indicators of compromise as they are released. CyFlare Pulse security subscribers can rest assured and are protected by our certified security analysts and around the clock monitoring of their network.
With AlienVault’s All-In-One SIEM platform we utilize Network IDS rules for detection of exploitation methods through the use of JavaScript and other methods to obfuscate malicious code. To date, there have been known exploits in the wild outside the POC listed above.
NIDS plugin event types detected attacks,
PID:1001, SID:2025184, AlienVault NIDS: “ET
WEB_CLIENT Spectre Kernel Memory Leakage JavaScript (POC Based)”
PID:1001, SID:2025185, AlienVault NIDS: “ET
WEB_CLIENT Spectre Kernel Memory Leakage JavaScript”
PID:1001, SID:2025188, AlienVault NIDS: “ET
WEB_CLIENT Spectre Exploit Javascript”
PID:1001, SID:2025196, AlienVault NIDS: “ET EXPLOIT
Possible Spectre PoC Download In Progress”
PID:1001, SID:2025195, AlienVault NIDS: “ET EXPLOIT
Possible MeltDown PoC Download In Progress”
Vulnerability systems are detected via authenticated vulnerability scans as new signatures are release by AlienVault and vulnerability reports are received by subscribers on a weekly basis.
Included with AlienVault is access to the worlds largest intelligence community through Open Threat Exchange (OTX). 65,000 members with 40,000 indicators of compromise created on a daily basis from multiple industry verticals. Subscriber network traffic is compared with known bad IP and domain reputation data and other metadata in real-time.
Recommendation for CyFlare SOC Subscribers
It is important to note that both exploitation techniques require local authentication and there is currently no remote attack capability. Our recommendations with input from the security community include,
- Ensuring the latest security patches have been applied across your environment
- Evaluate and Test patches in development before applying to production
- Have a strong backup strategy and plan in place
- Consult with mobile device manufactures to ensure patches are pushed properly through your MDM policy
- Ensuring the controls to restrict and control access to your infrastructure are strengthened and utilizing strong password policies
- Password length and complexity
- Account Lockout policy
- Restriction of access from remote systems to critical assets within the data center and cloud
- Usage of the least privilege model and network segmentation
- Train organization on how to watch for phishing attempts and how to report
- Evaluate the need for services (e.g. SMB) and disable those that are not required.
Other Resources
PowerShell script to verify protections are enabled release by Microsoft
https://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050
Registry Key settings in order to disable security fixes on a per machine bases if needed.


